YubiKey
Enterprise-grade hardware authentication for robust security.

Secure Your Enterprise with YubiKeys
In today’s digital landscape, security breaches are a constant threat to businesses of all sizes. Therefore, strong authentication is essential for protecting your enterprise. YubiKeys provide a robust and cost-effective solution for enhancing your security posture and mitigating the risk of data breaches. By implementing YubiKeys, you can protect your valuable data, maintain compliance, and improve the overall security of your organization.
Raising the bar by empowering users to be phishing-resistant
To stop modern threats you must have modern phishing-resistant authentication that moves with users no matter how they work across devices, platforms and systems. The YubiKey is hardware authentication reimagined. Secure the identities of your employees and users, reduce support costs, and experience an unmatched user experience.
0
account takeover
92%
reduction in support calls
4x
faster login
How the YubiKey works?
YubiKeys support multiple authentication protocols so you are able to use them across any tech stack, legacy or modern–flowing effortlessly with the user. No more reaching for your phone to open an app, or memorizing and typing in a code – simply touch the YubiKey to verify and you’re in. Once an app or service is verified, it can stay trusted. It’s that easy.
Easy to use across all devices

Insert YubiKey & touch
On a computer, insert the YubiKey into a USB-port and touch the key to verify you are human and not a remote hacker.
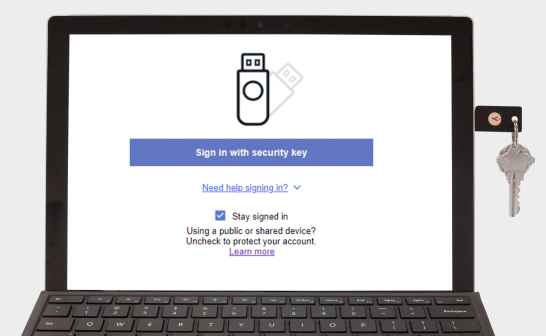
Register your YubiKey
To use the YubiKey, go to the Security Settings of a supported service and and select “Add Security Key”.

Tap YubiKey to device
Tap the YubiKey on NFC enabled devices. Once registered, many services will not require the key after first login – it just works!
Highest assurance authentication that’s fast and easy
Strongest 2FA
A physical security key, that can be added to a keychain and plugged into a computer, tablet or mobile device, adds an extra layer of protection on top of passwords to offer the strongest second factor authentication protection against phishing attacks.

Strongest MFA
Users can combine the hardware authenticator with a PIN or biometric to meet high assurance identity verification requirements before engaging in sensitive transactions.
Passwordless
Eliminate passwords altogether and move to a more secure and efficient account login experience with passwordless workflows, using the authenticator and PIN or biometric. Reduce calls to the helpdesk and therefore costs and downtime.
Authentication without Compromise
A single YubiKey has multiple functions for securing your login to email, online services, apps, computers, and even physical spaces. Use any feature, or use them all. The versatile key requires no software installation or battery so just plug it into a USB port and touch the button, or tap-n-go using NFC for secure authentication.
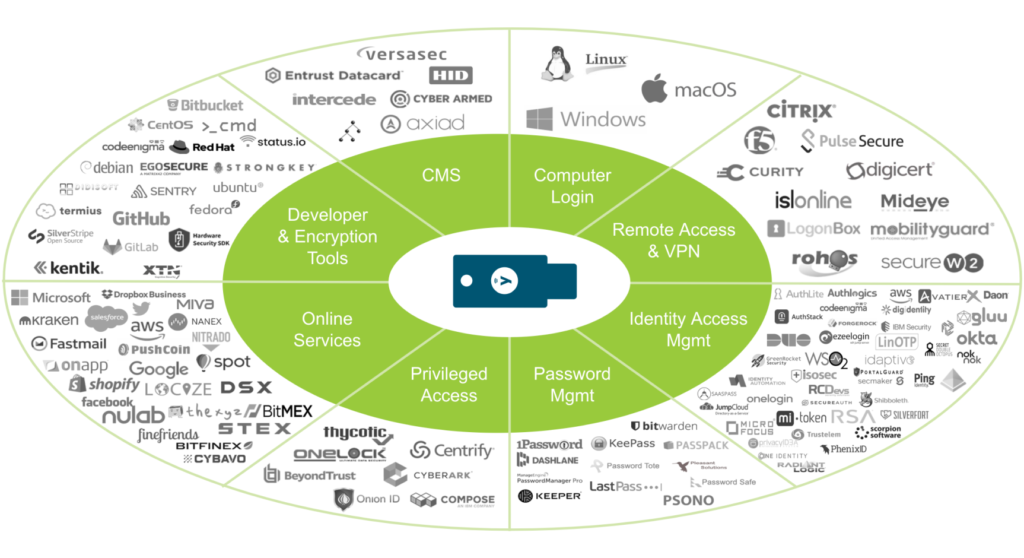
One Key to Access Them All
The YubiKey works with hundreds of enterprise, developer and consumer applications, out-of-the-box with no client software.
Contact Sales
Find the right key for you and your business.


